SAML (Security Assertion Markup Language) is an open standard for exchanging authentication and authorization data between parties, particularly between an identity provider (IdP) and a service provider (SP). It is widely used for Single Sign-On (SSO), enabling users to authenticate once and gain access to multiple applications without having to log in again.
Here’s how SAML works:
User Requests Access: A user attempts to access a service provider (SP) application, such as a web app or cloud service.
Redirect to Identity Provider (IdP): The service provider checks if the user is authenticated. If not, the user is redirected to an identity provider (IdP) like Google, Okta, or Active Directory.
Authentication at IdP: The user authenticates with the IdP, usually with a username and password. The IdP may also use multi-factor authentication (MFA) for added security.
SAML Assertion: After authentication, the IdP generates a SAML Assertion—an XML document containing the user’s authentication information and authorization details. This assertion is signed by the IdP to ensure its authenticity.
Assertion Sent to SP: The SAML assertion is sent back to the service provider (SP), typically via the user’s browser. This step is usually done via HTTP POST.
Verification and Access: The service provider verifies the authenticity of the SAML assertion, ensuring it’s from a trusted IdP. Once verified, the user is granted access to the requested resource.
Key Benefits of SAML Authentication #
- Single Sign-On (SSO): Users authenticate once with an IdP and can access multiple applications without needing to log in again.
- Improved Security: Credentials are only stored and managed by the IdP, reducing the risk of password theft at the SP level. The use of signed SAML assertions also ensures secure transmission of authentication data.
- Centralized User Management: Administrators can manage user identities centrally through the IdP, simplifying user provisioning, de-provisioning, and access control across applications.
- Reduced Password Fatigue: By reducing the need for multiple passwords, SAML enhances user experience and encourages better security practices.
Common Use Cases #
- Enterprise Applications: SAML is frequently used by large organizations to enable employees to authenticate across multiple internal and external applications with a single login.
- Cloud Service Access: Cloud-based platforms like AWS, GCP, and Salesforce support SAML authentication to allow users to access services with SSO.
- Education and Government: SAML is commonly used for Federated Identity Management in academic institutions and government agencies to provide SSO across various systems.
Overall, SAML is a highly secure and efficient method for handling authentication and authorization in environments where centralized user management is crucial.
Variable Used:
<nextcloud_server_url>: https://nextcloud.domain.com/index.php
<nextcloud_server_url>: https://nextcloud.domain.com/ [If index.php is disabled]
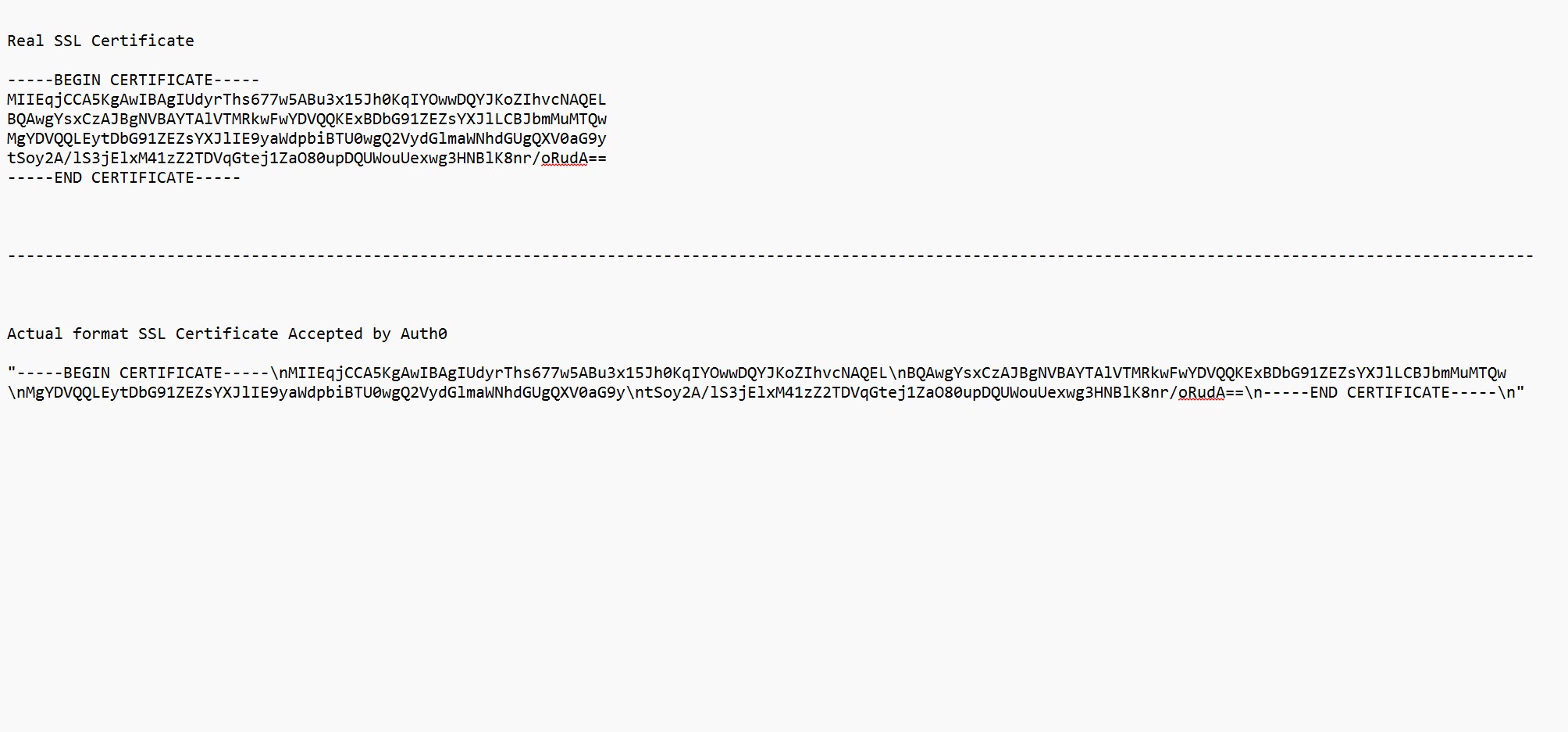
<ssl_crt>: It can be any SSL certificate or self-generated Certificate.
Note: for formatting instructions, you start with a PEM format certificate and replace the line endings with “\n”
<private_key>: The only private key of which the SSL is used or the self-generated Certificate.
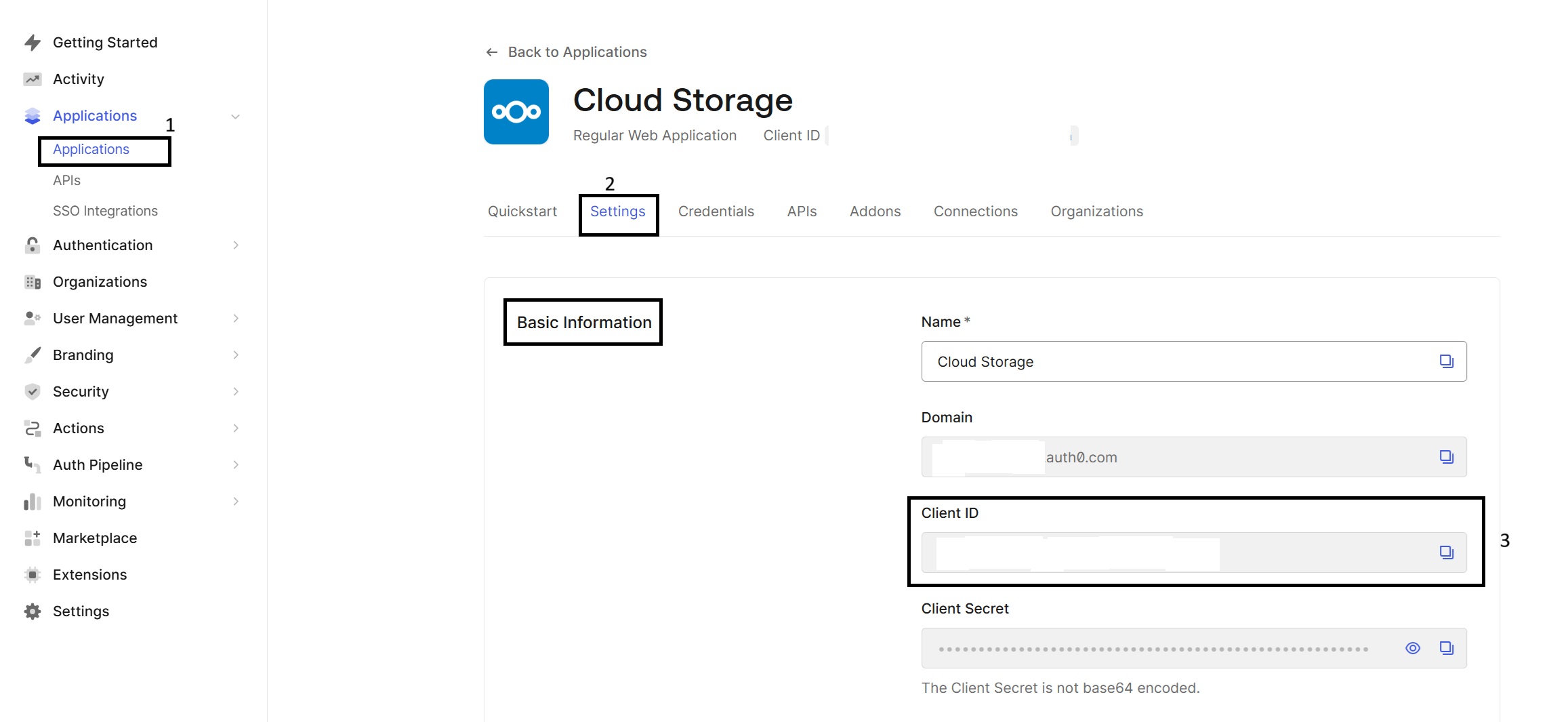
<client_id>: The Client ID which is available in the Basic Information of Settings of the Application.
1. Follow the below configuration to add it in your Auth0 #
Auth0 Configuration #
| SAML Protocol | Description |
|---|---|
| ACS URL | <nextcloud_server_url>/apps/user_saml/saml/acs |
| "audience" | <nextcloud_server_url>/apps/user_saml/saml/metadata |
| "recipient" | <nextcloud_server_url>/apps/user_saml/saml/acs |
| "nameIdentifierFormat" | urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress |
| "logout": "callback" | <nextcloud_server_url>/apps/user_saml/saml/sls |
| "logout": "slo_enabled" | true |
| "binding" | urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect |
| "signResponse" | false |
| "signatureAlgorithm" | rsa-sha256 |
| "signingCert" | <ssl_crt> |
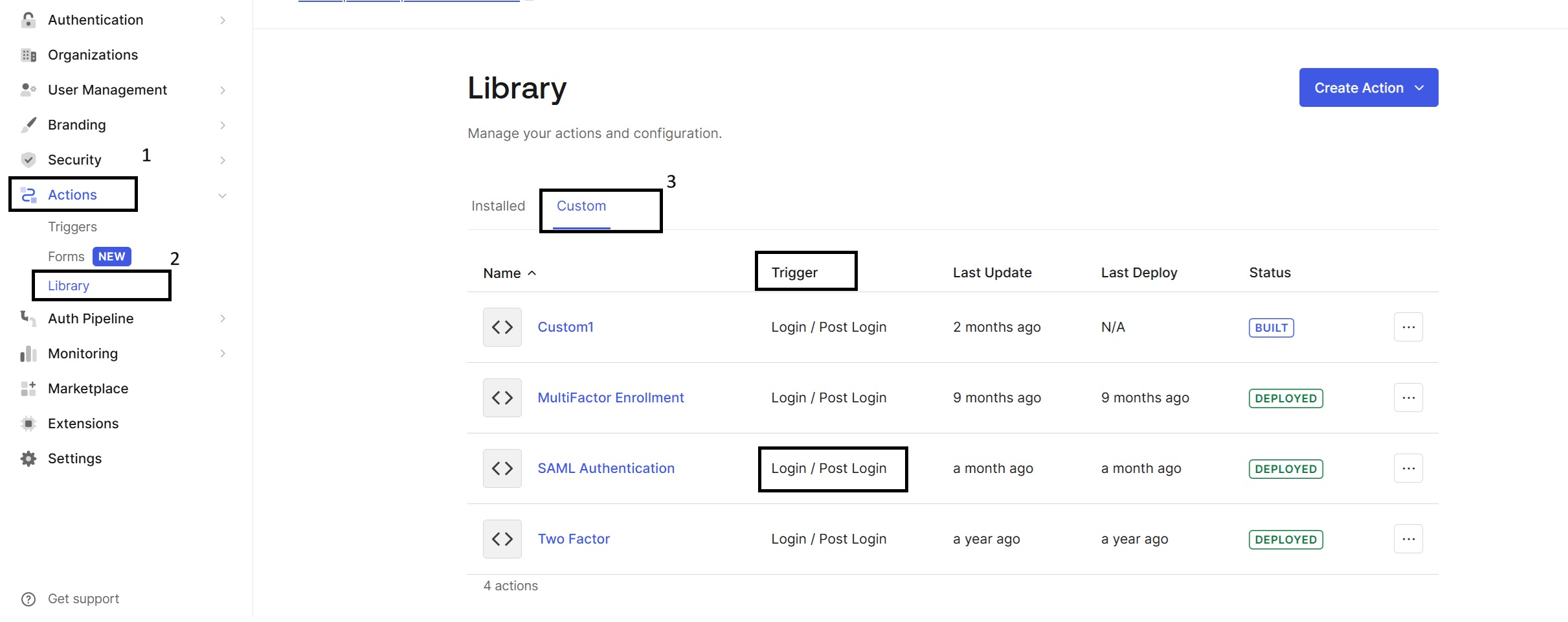
To also enable Encrypt Assertation with the signing of SAML with the below code in Action. To enable follow: Action > Library > Custom Action.
Use Trigger: Login / Post Login
Encryption Code #
Copied
exports.onExecutePostLogin = async (event, api) => {
// this Action sets a specific public key to encrypt the SAML assertion generated from Auth0
if (
event.client.client_id ===
"<client_id>"
) {
const encryptionCert =
"<ssl_crt>";
const encryptionPublicKey =
"<private_key>";
api.samlResponse.setEncryptionCert(encryptionCert);
api.samlResponse.setEncryptionPublicKey(encryptionPublicKey);
}
};
2. Follow the below configuration to add it in your Nextcloud #
Nextcloud Configuration #
| SAML Global Settings | Description |
|---|---|
| Attribute to map the UID to | username |
| Optional display name of the identity provider |
Auth0 |
| X.509 certificate of the Service Provider |
<ssl_crt> |
| Private key of the Service Provider |
<private_key> |
| Identifier of the IdP entity (must be a URI) or Entity ID |
urn:<tenantname.region.auth0.com> |
| URL Target of the IdP where the SP will send the Authentication Request Message or SingleSignOnService |
<tenant.region.auth0.com>/samlp/<client_id> |
| URL Location of the IdP where the SP will send the SLO Request or SingleLogoutService |
<tenant.region.auth0.com>/samlp/<client_id>/logout |
| URL Location of the IDP's SLO Response |
Same as above SLO URL |
| Public X.509 certificate of the IdP |
The Auth0 Certificate |